The Easiest Way To Disaster-Proof Your Cyber Security
Though no one would dispute the increasing prevalence of cyber-attacks on businesses in recent years, many small-business owners believe themselves and their business to be immune to such cyber attacks. Broadly speaking, many small-business owners are likely to think that cybercriminals will go after the bigger fish. However, the fact of the matter is that cyber-attacks are crimes of opportunity, and small businesses often have access to a good amount of sensitive data without many major safeguards. In other words, they’re low-hanging fruit, ripe for the picking.
Back in 2019, two-thirds of respondents to a survey about cyber security didn’t believe that their small to mid-size business (SMB) would fall victim to a cyber-attack. Consequently, only 9% of respondents said cyber security was a top priority for their business, and 60% didn’t have any sort of plan for deterring a cyber-attack. All of this, despite the fact that, according to a report from CNBC, SMBs endured 43% of reported cyber-attacks, and according to data from the Ponemon Institute and Keeper Security, 76% of SMBs in the U.S. alone reportedly endured a cyber-attack within the previous year.
Every small-business owner should have some plan for deterring cyber-attacks so they don’t end up as another statistic. Here are a few strategies for keeping the cybercriminals at bay.
Boost Your Cloud Security
Storing data in the cloud is easy and cost-effective, but you should take care to find the most secure cloud storage platforms. Not all cloud platforms make security a priority, but some do. A few of the top-rated, most secure cloud platforms, according to Cloudwards.net, include Sync.com, pCloud and Icedrive.
Secure All Parts Of Your Network
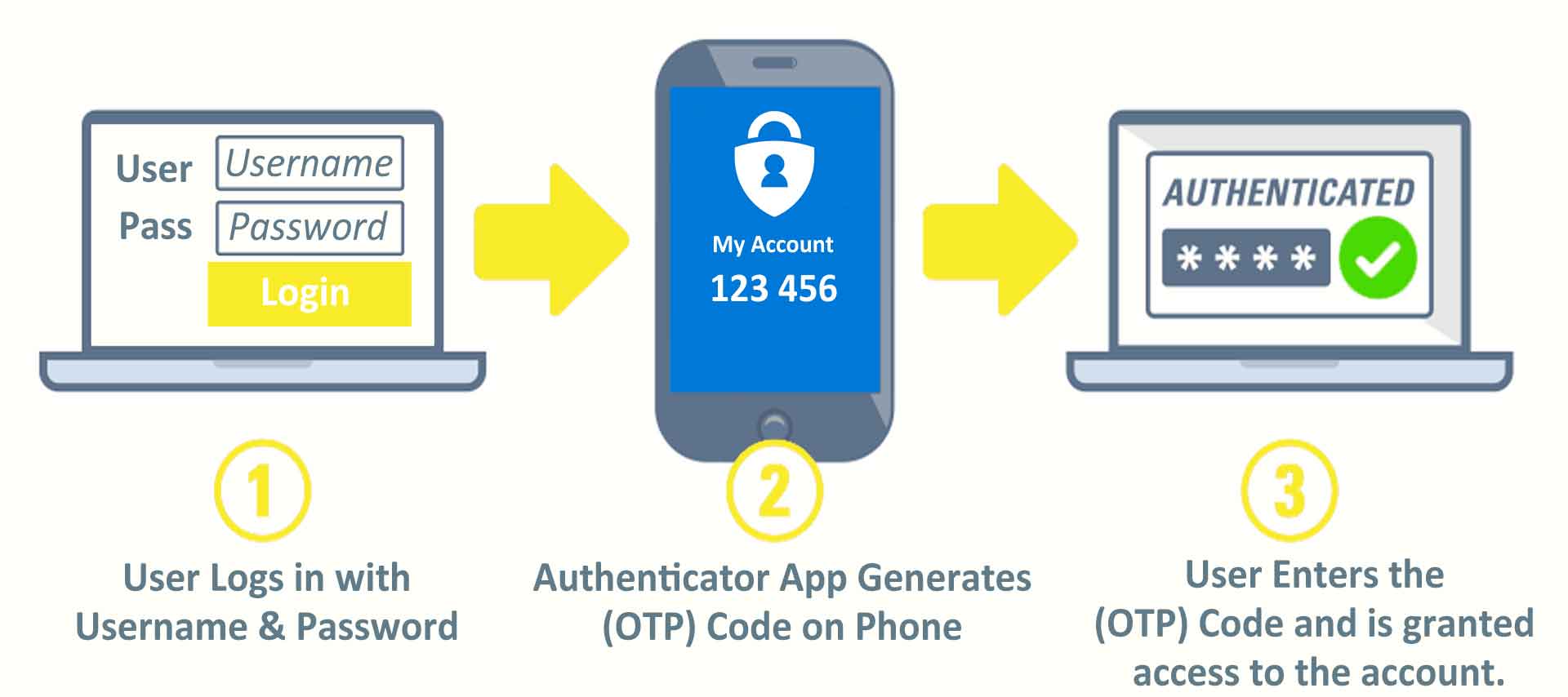
Our computers and the many smart devices hooked up to our network can become weak spots for hackers to get in. Taking steps to safeguard each device in your network with strong passwords and robust authentication measures will go a long way toward keeping the hackers at bay. In fact, one of the most basic security measures you can take for your network is to restrict access to your WiFi with a strong password.
Invest In Extra Security Measures
Virtual private networks (VPNs) and firewalls are tools that are highly effective in protecting against cyber-attacks, even if they can’t prevent 100% of them.
Pay Attention To Updates And Upgrades
When you get notified that one of the technological tools that you use has a new update, it’s easy to ignore it. However, you should commit to regularly updating and upgrading these tools because developers will often add patches to their programs that make them more secure against attacks with each update. So, it behooves business owners to regularly install updates for their tech tools.
Back Up Your Data
With one of the most common forms of cyber-attacks being ransomware attacks, where hackers will hold your company data hostage until you pay them a ransom amount, having your company data stored on multiple backup solutions can ensure that your business won’t crumble due to your data’s inaccessibility.
Limit Employee Access To Your Network
As much as we’d wish it were true, many cyber-attacks don’t come from outside of your company. Instead, they originate from within. If you want to limit the amount of damage that someone inside your company can do in a cyber-attack, the best course of action is to limit their access to different parts of your network.
Train Your Employees
At the same time, just as many cyber-attacks occur not because of an employee’s malicious intent, but because of their ignorance. They click on a link in a sketchy e-mail and fall for a phishing scheme, volunteer their password info without thinking about it or choose a weak password for their computer. That’s why you need to dedicate time to training your employees on best practices when it comes to security.
Set Up A ‘Security Culture’ At Your Workplace
You need to make cyber security a top priority, not just for your IT department, but for every department at your business. When everyone works together to protect their workplace from a cyber-attack, you have a better chance of actually succeeding.
Will protecting your business from a cyber-attack require a good amount of time and money? Absolutely. Can you afford to ignore the prevalence of cyber-attacks any longer? Statistically, no. The sad truth is that 60% of SMBs that fall victim to a cyber-attack end up shuttering within six months. Don’t put yourself in that kind of position. Instead, take your business’s cyber security seriously.