As hurricane season approaches, businesses must take proactive steps to safeguard their operations, data, and employees. Hurricanes pose significant risks, from physical damage to infrastructure to potential data loss and service interruptions. By preparing in advance, businesses can minimize disruptions and ensure a quick recovery. Here are essential tips for preparing for a hurricane, with a focus on business continuity and technology.
1. Create a Disaster Recovery Plan
A disaster recovery (DR) plan is essential for any business in hurricane-prone areas. Ensure your plan includes:
Clear steps for data backup and restoration: Regularly back up business-critical data both on-site and in the cloud. This ensures that if your physical infrastructure is damaged, you can quickly restore operations from a secure, off-site location.
Communication protocols: Establish emergency communication channels with employees, customers, and stakeholders. Make sure everyone knows how to stay updated during a disaster.
Critical business functions: Identify key services or systems that must be operational during or after the storm. Ensure these are prioritized in your DR plan.
2. Back Up Data to the Cloud
Data loss is one of the most significant risks during a hurricane. If local servers or infrastructure are compromised by flooding, power loss, or other damage, cloud-based backups are crucial.
Cloud-to-cloud backup solutions: Consider backing up services like Microsoft 365, Google Workspace, and other cloud applications. This ensures that even if your office is impacted, your business-critical data remains safe and accessible.
Automated backup systems: Schedule automated backups to reduce human error and ensure that data is continuously protected.
3. Protect Physical Equipment
If your business relies on physical technology like servers, computers, or networking equipment, it’s essential to safeguard these assets before the storm:
Elevate critical equipment: Raise important equipment off the floor in case of flooding. Use waterproof covers or protective cases.
Uninterruptible power supplies (UPS): Invest in UPS systems to provide backup power to servers and essential equipment, especially in areas prone to power outages. Ensure your UPS units are tested and functioning.
4. Implement Strong Cybersecurity Measures
While physical damage is often the most immediate concern, hurricanes can also expose businesses to cybersecurity threats:
Update security patches: Ensure that all devices, including workstations, servers, and network hardware, are up-to-date with the latest security patches.
Remote work readiness: In case your physical location becomes inaccessible, ensure that your employees are equipped for remote work with secure VPNs, multi-factor authentication, and other cybersecurity best practices to prevent unauthorized access.
Phishing and smishing awareness: Cybercriminals may take advantage of the chaos caused by natural disasters to launch phishing or smishing campaigns. Educate employees about these risks and establish a protocol for reporting suspicious emails or text messages.
5. Test Communication Systems
Before a hurricane hits, test your business’s communication systems to ensure they work during emergencies:
Emergency contacts: Update emergency contact lists for employees, vendors, and clients, and ensure they are accessible via multiple channels (email, phone, or text).
Automated alerts: Use automated systems to alert employees about any operational changes, office closures, or safety measures.
Virtual meeting platforms: Ensure employees have access to video conferencing tools to stay connected in case they cannot be physically present at the office.
6. Plan for Remote Work
If a hurricane disrupts normal business operations, having a remote work strategy is essential:
Access to company systems: Ensure that employees can access necessary systems and data remotely. This includes ensuring that cloud applications are functioning and accessible, and that remote desktop solutions are set up.
Cybersecurity for remote work: Strengthen your cybersecurity protocols for remote work, such as enforcing the use of strong passwords, VPNs, and encrypted communication tools.
7. Communicate with Clients and Customers
Clear communication is essential when a hurricane is threatening your area. Proactively inform clients and customers about potential service disruptions or delays.
Keep clients updated: If you anticipate delays or interruptions, communicate your plan to your clients and let them know when they can expect updates.
Offer alternatives: If your physical location is compromised, offer alternative methods for clients to engage with your services, such as online consultations or remote support.
Final Thoughts
Preparing for a hurricane is critical for protecting your business, your employees, and your technology infrastructure. By taking proactive measures such as implementing disaster recovery plans, backing up data to the cloud, securing physical equipment, and ensuring robust communication systems, your business can weather the storm and emerge resilient.
Stay safe and prepared—your business depends on it!



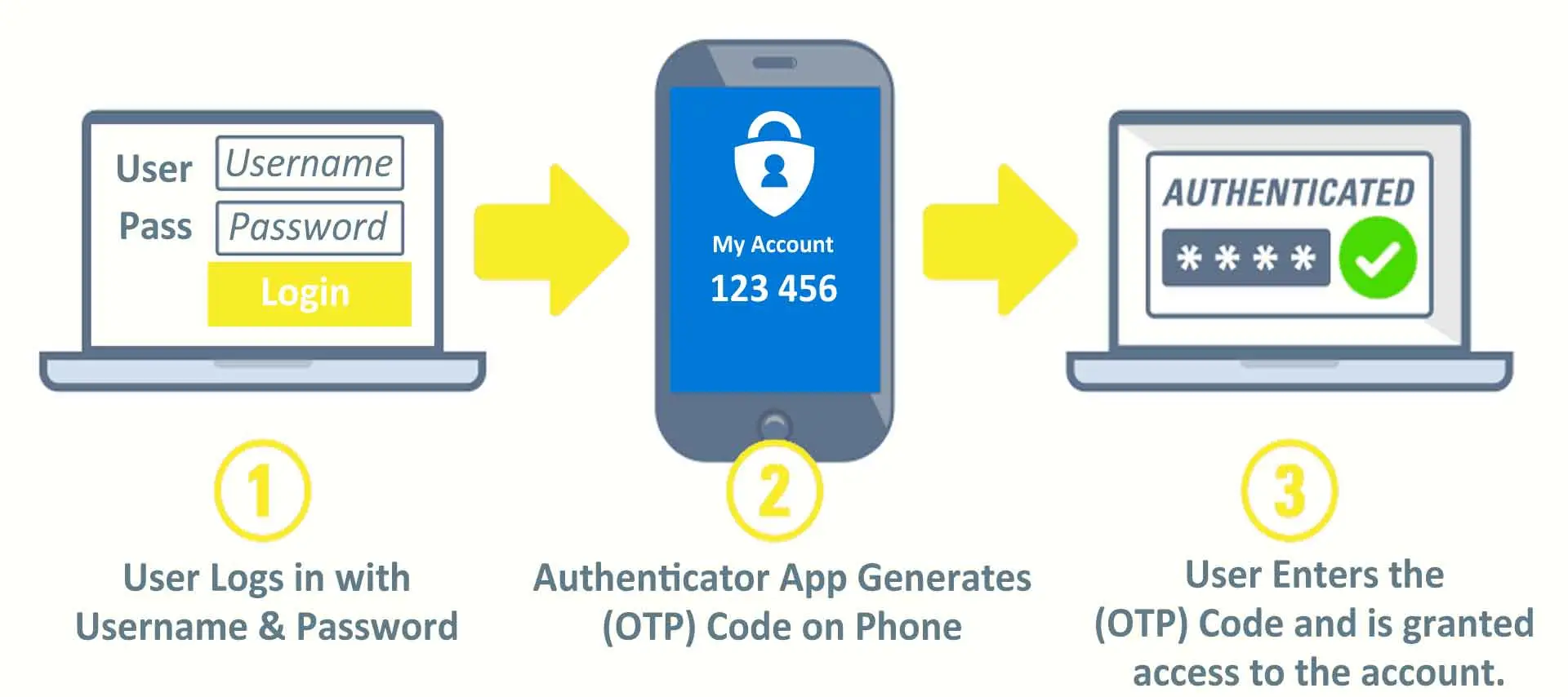

 There is a known issue with Microsoft’s March Security Patch Rollup (
There is a known issue with Microsoft’s March Security Patch Rollup (